 Cybersecurity firm Trend Micro has identified a modification to an older version of “malvertising” malware called Glupteba that uses Bitcoin script to keep it from being expunged off the Internet.
Cybersecurity firm Trend Micro has identified a modification to an older version of “malvertising” malware called Glupteba that uses Bitcoin script to keep it from being expunged off the Internet.
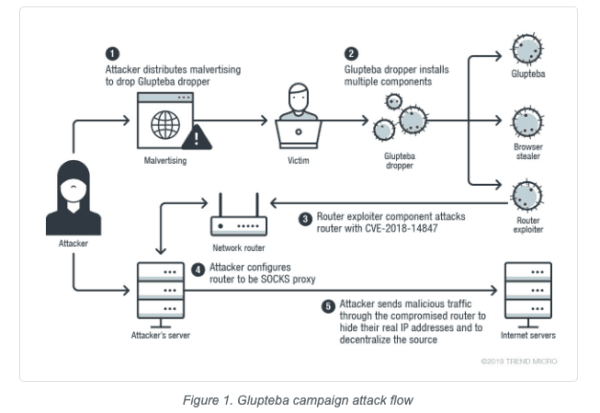
In addition to functioning as, “a browser stealer that can steal…browsing history, website cookies…account names and passwords from browsers,” the new ‘Glupteba dropper’ also uses Bitcoin to reconnect the malware with it’s command server in the event a connection is cut off.
According to Trend Micro:
“This technique makes it more convenient for the threat actor to replace C&C servers. If they lose control of a C&C server for any reason, they simply need to add a new Bitcoin script and the infected machines obtain a new C&C server by decrypting the script data and reconnecting.”
Gluptepa can also take over victims’ routers and use them hide the IP addresses of the malware network’s command servers.
Malware networks are often very broad and involve hundreds if not thousands of “zombified” computers forced by malicious code to send private data, receive malware updates or send the proceeds of crypto mining infections.
One way authorities contain malware is by shutting down command servers or breaking communication with them.
Bitcoin, however, runs on thousands of servers worldwide. Countering server-malware communication on one bitcoin “node” does nothing to stop communicating with other nodes.
“Cybergendarmes” from France’s C3N anti-cybercrime recently dismantled a botnet that infected 850 000 computers worldwide with a virus to mine the privacy cryptocurrency Monero, the BBC reported last week.
The cybergendarmes located and dismantled a malicious pirate server in Paris that functioned as the nerve centre of the botnet. They then moved on to disinfecting computers around the world by making a “replica server that rendered the virus inactive on the infected computers,” according to the BBC.
The botnet (a network of “zombified” computers commandeered by a virus to proliferate viruses) is believed to have generated millions of Euros in Monero since 2016.
Hackers used a server located in France to send out the “Retadup” virus in “phishing emails” (featuring erotic photos, for example), and also somehow proliferated infected USB drives
Police said the Retadup botnet was large enough to, “bring down all the websites on the planet.”
Trend Micro says enterprises and institutions should be very careful of the new, Bitcoin-borne Glupteba:
“Since it is already proven to be an information stealer and a proxy for malicious spam, users and enterprises should be wary of this threat.”
Trend Micro offers a number of software packages for defence against cyberattacks and corporate espionage, including Trend Micro™ Security, Trend Micro Network Defense, Trend Micro Smart Protection Suites and Trend Micro Worry-Free™ Business Security.

